Get Latest Exam Updates, Free Study materials and Tips

1.The Central Limit Theorem says that the sampling distribution of the sample mean is approximately normal if
a. all possible samples are selected.
b. the sample size is large.
c. the standard error of the sampling distribution is small.
Ans:B
2. The Central Limit Theorem says that the mean of the sampling distribution of the sample means is
a. equal to the population mean divided by the square root of the sample size.
b. close to the population mean if the sample size is large.
c. exactly equal to the population mean.
Ans:C
3. The Central Limit Theorem says that the standard deviation of the sampling distribution of the sample means is
a. equal to the population standard deviation divided by the square root of the sample size.
b. close to the population standard deviation if the sample size is large.
c. exactly equal to the standard deviation.
Ans: A
4. Samples of size 25 are selected from a population with mean 40 and standard deviation 7.5. The mean of the sampling distribution of sample means is
a. 7.5
b. 8
c. 40
Ans: C
5.Samples of size 25 are selected from a population with mean 40 and standard deviation 7.5. The standard error of the sampling distribution of sample means is
a. 0.3
b. 1.5
c. 7.5
Ans:C
6. Least Squares Estimation minimizes
a. summation of squares of errors
b. summation of errors
c. summation of absolute values of errors
d. All
ANS : A
7. Random variables give relationship between _____
a) Two random events
b) Probability of occurence of two random events
c) Random event and a real number
d) Random event and its probability of occurrence
Answer: c
Explanation: A random variable gives a functional relationship between a random event and a real number.
8. The distribution function of random variable is
a) P(X less than or equal to x)
b) P(X greater than or equal to x)
c) P(X less than x)
d) P(X greater than x)
Answer: a
Explanation: The distribution function of a random variable is the probability that the value taken by the random variable is less than or equal to the real number x.
9. The distribution function of -(infinity) and (infinity) is _____
a) 0 and 1
b) 1 and 0
c) Both 0
d) Both 1
Answer: a
Explanation: F(minus infinity) is 0 and F(infinity) is 1.
10. The value of the probability density function of random variable is
a) Positive function
b) Negative function
c) Zero
d) One
Answer: a
Explanation: The probability density function is always greater than 0. It is a non negative function with the area of 1.
11. Which gives the measure of randomness of the random variable?
a) Mean
b) Variance
c) Standard variance
d) Pdf
Answer: b
Explanation: Variance gives the randomness of the random variable. It is the difference between the mean square value and square of the mean.
12. Random process is a function of ______
a) Random event and time
b) Random event and frequency
c) Random event and real number
d) None of the mentioned
Answer: a
Explanation: Random process is a function of two variables: a random event and its time of occurrence.
13. A random process is called as stationary in strict sense if
a) Its statistics vary with shift in time origin
b) Its statistics does not vary with shift in time origin
c) Its autocorrelation vary with shift in time
d) Its autocorrelation does not vary with shift in time
Answer: a
Explanation: A random process is defined to be stationary in a strict sense if its statistics varies with a shift in time origin.
14. For a stationary process, autocorrelation function depends on
a) Time
b) Time difference
c) Does not depend on time
d) None of the mentioned
Answer: b
Explanation: Autocorrelation function depends on the time difference between t1 and t2.
15. The autocorrelation function is maximum at
a) Origin
b) Infinity
c) Origin & Infinity
d) None of the mentioned
Answer: a
Explanation: On substituting different values in the formula for autocorrelation function it wil be maximum at the origin.
16. Standard deviation is ______
a) Rms value of dc
b) Rms value or ac
c) Either ac or dc
d) Neither dc nor ac
Answer: b
Explanation: The standard deviation of a random variable gives the rms value of an ac component.
17. The average power of white noise is
a) Zero
b) Unity
c) Infinity
d) Between zero and one
Answer: c
Explanation: The average power of white noise is infinity because its bandwidth is infinite.
18. White noise has _____ mean and ______ variance.
a) Zero and zero
b) Finite and zero
c) Zero and finite
d) One and zero
Answer: c
Explanation: White noise is a zero mean function with infinite average power, finite variance and infinite bandwidth.
1. The minimum nyquist bandwidth needed for baseband transmission of Rs symbols per second is
a) Rs
b) 2Rs
c) Rs/2
d) Rs2
Answer: c
Explanation: Theoretical minimum nyquist bandwidth needed for the baseband transmission of Rs symbols per second without ISI is Rs/2.
2. The capacity relationship is given by
a) C = W log2 ( 1+S/N )
b) C = 2W log2 ( 1+S/N )
c) C = W log2 ( 1-S/N )
d) C = W log10 ( 1+S/N )
Answer: a
Explanation: The capacity relationship from Shannon-hartley capacity theorem is given by C = W log2 ( 1+S/N ).
3. Which parameter is called as Shannon limit?
a) PB/N0
b) EB/N0
c) EBN0
d) None of the mentioned
Answer: b
Explanation: There exists a limiting value for EB/N0 below which they can be no error free communication at any information rate. This EB/N0 is called as Shannon limit.
4. Entropy is the measure of
a) Amount of information at the output
b) Amount of information that can be transmitted
c) Number of error bits from total number of bits
d) None of the mentioned
Answer: a
Explanation: Entropy is defined as the average amount of information per source output.
5. Equivocation is the
a) Conditional entropy
b) Joint entropy
c) Individual entropy
d) None of the mentioned
Answer: a
Explanation: Shannon uses a correction factor called equivocation to account for uncertainty in the received signal. It is defined as the conditional entropy of the message X given Y.
6. For a error free channel, conditional probability should be
a) Zero
b) One
c) Equal to joint probability
d) Equal to individual probability
Answer: a
Explanation: For a error free channel conditional probability should be zero, because having received Y there is complete certainty about the message X.
7. Average effective information is obtained by
a) Subtracting equivocation from entropy
b) Adding equivocation with entropy
c) Ratio of number of error bits by total number of bits
d) None of the mentioned
Answer: a
Explanation: According to Shannon the average effective information is obtained by subtracting the equivocation from the entropy of the source.
8. Turbo codes are
a) Forward error correction codes
b) Backward error correction codes
c) Error detection codes
d) None of the mentioned
Answer: a
Explanation: Turbo codes are a class of high performance forward error correction codes.
9. Components used for generation of turbo codes are
a) Inter leavers
b) Punching pattern
c) Inter leavers & Punching pattern
d) None of the mentioned
Answer: c
Explanation: There are many instances of turbo codes, using different component encoders, input/output ratios, inter leavers, punching patterns.
10. Decoders are connected in series.
a) True
b) False
Answer: a
Explanation: Two elementary decoders are connected in serial connection for decoding the turbo codes.
11. The inter leaver connected between the two decoders is used to
a) Remove error bursts
b) Scatter error bursts
c) Add error bursts
d) None of the mentioned
Answer: b
Explanation: An inter leaver installed between the two decoders connected in series is used to scatter error bursts.
12. In soft decision approach what does -127 mean?
a) Certainly one
b) Certainly zero
c) Very likely zero
d) Very likely one
Answer: b
Explanation: The decoder front end produces an integer for each bit in the data stream. This integer is the measure of how likely it is that the bit 0 or 1 and is called as soft bit. It ranges from -127 to 127. Here -127 represents certainly zero.
13. In soft decision approach 100 means?
a) Certainly one
b) Certainly zero
c) Very likely zero
d) Very likely one
Answer: d
Explanation: The decoder front end produces an integer for each bit in the data stream. This integer is the measure of how likely it is that the bit 0 or 1 and is called as soft bit. It ranges from -127 to 127. Here 100 represents very likely one.
14. In soft decision approach 0 represents
a) Certainly one
b) Certainly zero
c) Very likely zero
d) Could be either zero or one
Answer: d
Explanation: The decoder front end produces an integer for each bit in the data stream. This integer is the measure of how likely it is that the bit 0 or 1 and is called as soft bit. It ranges from -127 to 127. Here 0 represents ‘could be either zero or one’.
15. For a binary symmetric channel, the random bits are given as
a) Logic 1 given by probability P and logic 0 by (1-P)
b) Logic 1 given by probability 1-P and logic 0 by P
c) Logic 1 given by probability P2 and logic 0 by 1-P
d) Logic 1 given by probability P and logic 0 by (1-P)2
ANSWER: a) Logic 1 given by probability P and logic 0 by (1-P)
16.The channel capacity according to Shannon’s equation is
a) Maximum error free communication
b) Defined for optimum system
c) Information transmitted
d) All of the above
ANSWER: d) All of the above
17.For M equally likely messages, M>>1, if the rate of information R > C, the probability of error i
a) Arbitrarily small
b) Close to unity
c) Not predictable
d) Unknown
ANSWER: b) Close to unity
18. For M equally likely messages, M>>1, if the rate of information R <= C, the probability of error is
a) Arbitrarily small
b) Close to unity
c) Not predictable
d) Unknown
ANSWER: a) Arbitrarily small
19.The negative statement for Shannon’s theorem states that
a) If R > C, the error probability increases towards Unity
b) If R < C, the error probability is very small
c) None of the above
d) Not applicable
ANSWER: a) If R>C, the error probability increases towards Unity
20.According to Shannon Hartley theorem,
a) the channel capacity becomes infinite with infinite bandwidth
b) the channel capacity does not become infinite with infinite bandwidth
c) Has a tradeoff between bandwidth and Signal to noise ratio
d) Both b) and c) are correct
ANSWER: d) Both b) and c) are correct
21) Information rate basically gives an idea about the generated information per _____ by source.
a. Second
b. Minute
c. Hour
d. None of the above
ANSWER: Second
22) Which among the following is used to construct the binary code that satisfies the prefix condition?
a. Information Rate
b. Noiseless Channel
c. Channel Coding Theorem
d. Kraft Inequality
ANSWER: Kraft Inequality
23) Which coding technique/s exhibit/s the usability of fixed length codes?
a. Lempel Ziv
b. Huffman
c. Both a and b
d. None of the above
ANSWER: Lempel Ziv
24) Which lossy method for audio compression is responsible for encoding the difference between two consecutive samples?
a. Silence Compression
b. Linear Predictive Coding (LPC)
c. Adaptive Differential Pulse Code modulation (ADPCM)
d. Code Excited Linear Predictor (CELP)
ANSWER: Adaptive Differential Pulse Code modulation (ADPCM)
25) Which among the following compression techniques is/are intended for still images?
a. JPEG
b. H.263
c. MPEG
d. All of the above
ANSWER: JPEG
26) In dictionary techniques for data compaction, which approach of building dictionary is used for the prior knowledge of probability of the frequently occurring patterns?
a. Static Dictionary
b. Adaptive Dictionary
c. Both a and b
d. None of the above
ANSWER: Static Dictionary
27) Which bitmap file format/s support/s the Run Length Encoding (RLE)?
a. TIFF
b. BMP
c. PCX
d. All of the above
ANSWER: All of the above
28) Huffman coding technique is adopted for constructing the source code with ________ redundancy.
a. Maximum
b. Constant
c. Minimum
d. Unpredictable
ANSWER: Minimum
29) Which coding terminology deals with the inverse operation of assigned words of second language corresponding to the words in the first language?
a. Enciphering
b. Deciphering
c. Codeword
d. Codebook
ANSWER: Deciphering
30) In discrete memoryless source, the current letter produced by a source is statistically independent of _____
a. Past output
b. Future output
c. Both a and b
d. None of the above
ANSWER: Both a and b
31. Which of the following algorithms is the best approach for solving Huffman codes?
a) exhaustive search
b) greedy algorithm
c) brute force algorithm
d) divide and conquer algorithm
Answer: b
Explanation: Greedy algorithm is the best approach for solving the Huffman codes problem since it greedily searches for an optimal solution.
32. How many printable characters does the ASCII character set consists of?
a) 120
b) 128
c) 100
d) 98
Answer: c
Explanation: Out of 128 characters in an ASCII set, roughly, only 100 characters are printable while the rest are non-printable.
33. Which bit is reserved as a parity bit in an ASCII set?
a) first
b) seventh
c) eighth
d) tenth
Answer: c
Explanation: In an ASCII character set, seven bits are reserved for character representation while the eighth bit is a parity bit.
34. How many bits are needed for standard encoding if the size of the character set is X?
a) log X
b) X+1
c) 2X
d) X2
Answer: a
Explanation: If the size of the character set is X, then [log X] bits are needed for representation in a standard encoding.
35. The code length does not depend on the frequency of occurrence of characters.
a) true
b) false
Answer: b
Explanation: The code length depends on the frequency of occurrence of characters. The more frequent the character occurs, the less is the length of the code.
36. In Huffman coding, data in a tree always occur?
a) roots
b) leaves
c) left sub trees
d) right sub trees
Answer: b
Explanation: In Huffman encoding, data is always stored at the leaves of a tree inorder to compute the codeword effectively.
37. From the following given tree, what is the code word for the character ‘a’?
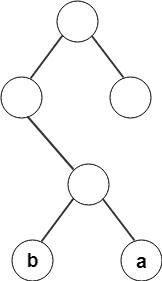
a) 011
b) 010
c) 100
d) 101
Answer: a
Explanation: By recording the path of the node from root to leaf, the code word for character ‘a’ is found to be 011.
38. From the following given tree, what is the computed codeword for ‘c’?
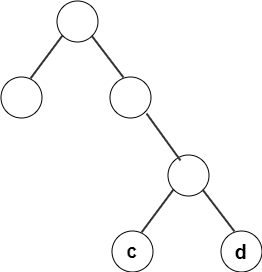
a) 111
b) 101
c) 110
d) 011
Answer: c
Explanation: By recording the path of the node from root to leaf, assigning left branch as 0 and right branch as 1, the codeword for c is 110.
39. What will be the cost of the code if character ci is at depth di and occurs at frequency fi?
a) cifi
b) ∫cifi
c) ∑fidi
d) fidi
Answer: c
Explanation: If character ci is at depth di and occurs at frequency fi, the cost of the codeword obtained is ∑fidi.
40. An optimal code will always be present in a full tree.
a) true
b) false
Answer: a
Explanation: An optimal tree will always have the property that all nodes are either leaves or have two children. Otherwise, nodes with one child could move up a level.
41. The type of encoding where no character code is the prefix of another character code is called?
a) optimal encoding
b) prefix encoding
c) frequency encoding
d) trie encoding
Answer: b
Explanation: Even if the character codes are of different lengths, the encoding where no character code is the prefix of another character code is called prefix encoding.
42. What is the running time of the Huffman encoding algorithm?
a) O(C)
b) O(log C)
c) O(C log C)
d) O( N log C)
Answer: c
Explanation: If we maintain the trees in a priority queue, ordered by weight, then the running time is given by O(C log C).
43. What is the running time of the Huffman algorithm, if its implementation of the priority queue is done using linked lists?
a) O(C)
b) O(log C)
c) O(C log C)
d) O(C2)
Answer: d
Explanation: If the implementation of the priority queue is done using linked lists, the running time of Huffman algorithm is O(C2).
44. For M equally likely messages, M>>1, if the rate of informaon R > C,
the probability of error is
a) Arbitrarily small
b) Close to unity
c) Not predictable
d) Unknown
Ans:B
44. For M equally likely messages, M>>1, if the rate of informaon R = C,
the probability of error is
a) Arbitrarily small
b) Close to unity
c) Not predictable
d) Unknown
Ans:A
45. The negative statement for Shannon’s theorem states that
a) If R is greater than C, the error probability increases towards Unity
b) If R is less than C, the error probability is very small
c) Both a & b
d) None of the above
Ans:A
46. According to Shannon Hartley theorem,
a) The channel capacity becomes infinite with infinite bandwidth
b) The channel capacity does not become infinite with infinite bandwidth
c) Has a trade off between bandwidth and Signal to noise rao
d) Both b and c are correct
Ans:D
47. The capacity of a binary symmetric channel, given H(P) is binary
entropy funcon is
a) 1 – H(P)
b) H(P) – 1
c) 1 – H(P)2
d) H(P)2 – 1
Ans:A
1.For a (7, 4) block code, 7 is the total number of bits and 4 is the number of
a) Information bits
b) Redundant bits
c) Total bits- information bits
d) None of the above
ANSWER: a) Information bits
2.Interleaving process permits a burst of B bits, with l as consecutive code bits and t errors when
a) B <= 2tl
b) B >= tl
c) B <= tl/2
d) B <= tl
ANSWER: d) B <= tl
3.The code in convolution coding is generated using
a) EX-OR logic
b) AND logic
c) OR logic
d) None of the above
ANSWER: a) EX-OR logic
4.For decoding in convolution coding, in a code tree,
a) Diverge upward when a bit is 0 and diverge downward when the bit is 1
b) Diverge downward when a bit is 0 and diverge upward when the bit is 1
c) Diverge left when a bit is 0 and diverge right when the bit is 1
d) Diverge right when a bit is 0 and diverge left when the bit is 1
ANSWER: a) Diverge upward when a bit is 0 and diverge downward when the bit is 1
5.A linear code
a) Sum of code words is also a code word
b) All- zero code word is a code word
c) Minimum hamming distance between two code words is equal to weight of any non zero code word
d) All of the above
ANSWER: d) All of the above
6.Graphical representation of linear block code is known as
a) Pi graph
b) Matrix
c) Tanner graph
d) None of the above
ANSWER: c) Tanner graph
7. The cyclic codes are designed using
a) Shift registers with feedback
b) Shift registers without feedback
c) Flipflops
d) None of the mentioned
Answer: a
Explanation: The cyclic codes are a subclass of linear codes. It is designed using feedback shift registers.
8. A cyclic code can be generated using
a) Generator polynomial
b) Generator matrix
c) Generator polynomial & matrix
d) None of the mentioned
Answer: a
Explanation: A cyclic code can be generated using generator polynomial and block codes can be generated using generator matrix.
9. The feedback shift register circuit is called as
a) Multiplying circuit
b) Dividing circuit
c) Feedback circuit
d) Shifting circuit
Answer: b
Explanation: The cyclic shift of a code-word polynomial and encoding involves division of one polynomial by another. Thus this feedback shift register is also called as dividing circuit.
10. In the dividing circuit, the parity polynomial is obtained by the
a) Quotient
b) Remainder
c) Dividend
d) Divisor
Answer: b
Explanation: The parity polynomial is the remainder after diving by the generator polynomial it is available in the register after n shifts through the n-k stage feedback registers.
11. The received code contains an error if the syndrome vector is
a) Zero
b) Non zero
c) Infinity
d) None of the mentioned
Answer: b
Explanation: If the syndrome is an all zero vector then the received code-word is a valid code. If the syndrome is a non zero vector then the received code has errors.
12. Block codes are generated using
a) Generator polynomial
b) Generator matrix
c) Generator polynomial & matrix
d) None of the mentioned
Answer: b
Explanation: Block codes are generated using generator matrix and cyclic codes are generated using generator polynomial.
13. Extended go-lay code is formed by
a) Adding overall parity bit to perfect go-lay code
b) Ex-oaring overall parity bit with perfect go-lay code
c) Ex-oaring each bit of go-lay code
d) Dividing the overall parity bit with perfect go-lay code
Answer: a
Explanation: Extended go-lay code is formed by adding overall parity bit with the perfect bit known as the golay code.
14. Block length is the _____________ in the code word.
a) Number of elements
b) Distance between elements
c) Number of parity bits
d) None of the mentioned
Answer: a
Explanation: The block length n is the number of elements in the code word.
15. The rate of a block code is the ration of
a) Block length to message length
b) Message length to block length
c) Message weight to block length
d) None of the mentioned
Answer: b
Explanation: The rate of a block code is the ratio between its message length and the block length, R=k/n.
16. Linear codes are used for
a) Forward error correction
b) Backward error correction
c) Forward error detection
d) Backward error detection
Answer: a
Explanation: Linear codes are used in forward error correction. It allows for more efficient encoding and decoding procedures.
17. The k-bit message forms ____ distinct messages which is referred to as k-tuples.
a) 2k
b) K2
c) 2k
d) 21/k
Answer: c
Explanation: The k bit messages for 2k distinct message sequences which are referred to as k-tuples or sequence of k digits.
18. The sum of any two vectors in subset S is also in S. This is called as
a) Addition property
b) Subset property
c) Closure property
d) Similarity property
Answer: c
Explanation: The closure property states that the sum of any two vectors in subset S is also in S.
19. To avoid corruption during transmission, the code-word should be
a) Near
b) Far apart
c) Far
d) None of the mentioned
Answer: b
Explanation: The code-words should be far apart from one and another as possible so even when the vectors experience some corruption they may still be correctly decoded.
20. In a standard matrix set code-word there are _______ cosset.
a) 2k
b) 2n+k
c) 2n-k
d) 2n
Answer: c
Explanation: Each n-tuple appears in only one location none are missing and none are replicated. There are 2n-k cosets.
21. Syndrome is calculated by
a) HT/r
b) rHT
c) rH
d) None of the mentioned
Answer: b
Explanation: The syndrome is calculated using S=rHT.
22. The _____ of the code-word is the number of non zero elements.
a) Size
b) Weight
c) Distance
d) Subspace
Answer: b
Explanation: The size of the code-word is the number of code words. The weight of the code word can be given as the number of non zero elements and the distance between two code words is the hamming distance between them.
23. Some examples of linear codes
a) Hamming code
b) Reed-Solomon code
c) Parity code
d) All of the mentioned
Answer: d
Explanation: Some examples of linear codes are block codes, parity codes, reed-Solomon codes, hamming code, cyclic codes, polynomial codes, go-lay codes etc.
24. In layering, n layers provide service to
a) n layer
b) n-1 layer
c) n+1 layer
d) none of the mentioned
Answer: c
Explanation: In layering n layer provides service to n+1 layer and use the service provided by n-1 layer.
25. Which can be used as an intermediate device in between transmitter entity and receiver entity?
a) IP router
b) Microwave router
c) Telephone switch
d) All of the mentioned
Answer: d
Explanation: IP router, microwave router and telephone switch can be used as an intermediate device between communication of two entities.
26. Which has comparatively high frequency component?
a) Sine wave
b) Cosine wave
c) Square wave
d) None of the mentioned
Answer: c
Explanation: Square wave has comparatively high frequency component in them.
27. Which has continuous transmission?
a) Asynchronous
b) Synchronous
c) Asynchronous & Synchronous
d) None of the mentioned
Answer: b
Explanation: Synchronous has continuous transmission where as asynchronous have sporadic transmission.
28. Which requires bit transitions?
a) Asynchronous
b) Synchronous
c) Asynchronous & Synchronous
d) None of the mentioned
Answer: b
Explanation: Synchronous transmission needs bit transition.
29. In synchronous transmission, receiver must stay synchronous for
a) 4 bits
b) 8 bits
c) 9 bits
d) 16 bits
Answer: c
Explanation: In synchronous transmission, receiver must stay synchronous for 9 bits.
30. How error detection and correction is done?
a) By passing it through equalizer
b) By passing it through filter
c) By amplifying it
d) By adding redundancy bits
Answer: d
Explanation: Error can be detected and corrected by adding additional information that is by adding redundancy bits.
31. Which is more efficient?
a) Parity check
b) Cyclic redundancy check
c) Parity & Cyclic redundancy check
d) None of the mentioned
Answer: b
Explanation: Cyclic redundancy check is more efficient than parity check.
32. Which can detect two bit errors?
a) Parity check
b) Cyclic redundancy check
c) Parity & Cyclic redundancy check
d) None of the mentioned
Answer: b
Explanation: CRC is more powerful and it can detect various kind of errors like 2 bit errors.
33. CRC uses
a) Multiplication
b) Binary division
c) Multiplication & Binary division
d) None of the mentioned
Answer: c
Explanation: CRC uses more math like multiplication and binary division.
34. Which needs re-sending of signal?
a) Error correction
b) Error detection
c) Error correction & detection
d) None of the mentioned
Answer: b
Explanation: Error detection needs re-sending of data.
35. Which needs more check bits?
a) Error correction
b) Error detection
c) Error correction & detection
d) None of the mentioned
Answer: a
Explanation: Error correction needs more check bits where as error detection needs less check bits.
36. Which gets less affected by noise?
a) Error correction
b) Error detection
c) Error correction & detection
d) None of the mentioned
Answer: b
Explanation: Error detection is less affected by noise.
37. Which is used to protect privacy of the information?
a) Compression coding
b) Source coding
c) Cipher coding
d) None of the mentioned
Answer: c
Explanation: Cipher coding is used to provide privacy for the information.
38. Digital signals are easy for
a) Storage
b) Handling
c) Time dilation
d) All of the mentioned
Answer: d
Explanation: Digital signals have ease of handing, storage and time dilation.
39. Which are forward error correcting codes?
a) Block codes
b) Convolutional codes
c) Block & Convolutional codes
d) None of the mentioned
Answer: c
Explanation: Block codes and convolutional codes are examples of forward error correcting codes.
40. Which operates on continuous stream of data?
a) Block codes
b) Convolutional codes
c) Block & Convolutional codes
d) None of the mentioned
Answer: b
Explanation: Convolutional codes operates on a continuous stream of data.
41. Which is more complex?
a) Encoding
b) Decoding
c) Encoding & Decoding
d) None of the mentioned
Answer: b
Explanation: In the case of block codes, decoding is a complex method.
42. Which has better minimum distance?
a) Check sum
b) Cyclic redundancy check
c) Check sum & Cyclic redundancy check
d) None of the mentioned
Answer: b
Explanation: Cyclic redundancy check has better distances.
43. In symmetric key cryptosystem, who knows the key?
a) Sender
b) Receiver
c) Sender & Receiver
d) None of the mentioned
Answer: c
Explanation: In symmetric key cryptosystem, both sender and receiver knows the same key.
1. Wavelength and antenna size are related as
a) λ/2
b) λ/4
c) 2λ
d) 4λ
Answer: b
Explanation: The transmission of Em field in space is done with the help of antennas. Antenna size depends of the wavelength. The length of the antenna is equal to λ/4.
2. The detection method where carrier’s phase is given importance is called as
a) Coherent detection
b) Non coherent detection
c) Coherent detection & Non coherent detection
d) None of the mentioned
Answer: a
Explanation: When the receiver uses carrier’s phase as major factor for detection then it is called as coherent detection and when carrier is not given importance it is called as non coherent detection.
3. The coherent modulation techniques are
a) PSK
b) FSK
c) ASK
d) All of the mentioned
Answer: d
Explanation: Some of the examples of coherent modulation techniques are phase shift keying, amplitude shift keying, frequency shift keying and continuous phase modulation.
4. The real part of a sinusoid carrier wave is called as
a) Inphase
b) Quadrature
c) Inphase & Quadrature
d) None of the mentioned
Answer: a
Explanation: The two main parts of sinusoid carrier wave – real part is called as inphase and the imaginary part is called as quadrature.
5. Antipodal signal sets are those vectors that can be illustrated as
a) Two 180 opposing vector
b) Two 90 opposing vector
c) Two 360 opposing vector
d) None of the mentioned
Answer: a
Explanation: In BPSK the two vectors, the signal set can be illustrated as two 180 opposing vector which is called as antipodal signal sets.
6. The FSK signal which has a gentle shift from one frequency level to another is called as
a) Differential PSK
b) Continuous PSK
c) Differential & Continuous PSK
d) None of the mentioned
Answer: b
Explanation: In general FSK the signal change from one frequency to another will be abrupt but in continuous FSK the signal change from one frequency to another will be gentle and gradual.
7. Which modulation scheme is also called as on-off keying method?
a) ASK
b) FSK
c) PSK
d) GMSK
Answer: a
Explanation: In ASK modulation scheme the signal attains either maximum amplitude or zero point. Thus it is also called as on-off keying.
8. In amplitude phase keying each phase vector is separated by
a) 90
b) 0
c) 45
d) 180
Answer: c
Explanation: The combination of ASK and PSK is called as APK. In APK each vector is separated by 45.
9. The term heterodyning refers to
a) Frequency conversion
b) Frequency mixing
c) Frequency conversion & mixing
d) None of the mentioned
Answer: c
Explanation: The term heterodyning means frequency conversion and frequency mixing that yields a spectral shift in the signal.
10. The transformation of the waveform into a single point in signal space is called as
a) Vector point
b) Predetection point
c) Preamplification point
d) Transformation point
Answer: b
Explanation: The first step of the detection process is to reduce waveform into a single or group of random variable. This first step in the transformation of waveform into a point in signal space. This point is called as predetection point.
11. The limit which represents the threshold Eb/N0 value below which reliable communication cannot be maintained is called as
a) Probability limit
b) Error limit
c) Shannon limit
d) Communication limit
Answer: c
Explanation: Eb/N0 curve has waterfall shape. Shannon limit gives the threshold value below which reliable communication cannot be maintained.
12. M-ary signalling produces _______ error performance with orthogonal signalling and _______ error performance with multiple phase signalling.
a) Degraded, improved
b) Improved, degraded
c) Improved, improved
d) Degraded, degraded
Answer: b
Explanation: In M-ary signalling as k increases, the curve moves towards the degraded error performance. It produces improved error performance in case of orthogonal signalling and degraded error performance in case of multiple phase signalling.
13. Which is more vulnerable to noise?
a) 2-ary system
b) 4-ary system
c) Binary system
d) None of the mentioned
Answer: b
Explanation: The minimum energy noise vector for 4-ary system is smaller than 2-ary system. So 4-ary system is more vulnerable to noise.
14. In which system, bit stream is portioned into even and odd stream?
a) BPSK
b) MSK
c) QPSK
d) FSK
Answer: c
Explanation: In QPSK bit stream is portioned into even and odd stream, I and Q bit streams. Each new stream modulates as orthogonal component at half bit rate.
15. The error performance of MPSK ______ as M or k increases.
a) Increases
b) Decreases
c) Stays constant
d) None of the mentioned
Answer: b
Explanation: The error performance of MPSK degrades as M or k increases.
16. In MPSK adding new signals _______ make it vulnerable to noise and in MFSK _______ make it vulnerable.
a) Does, does not
b) Does not, does
c) Does, does
d) Does not, does not
Answer: a
Explanation: In MPSK adding new signals that is on crowding the signals it makes it vulnerable to noise where as in MFSK it does not.
17. In orthogonal signalling with symbols containing more number of bits we need ____ power.
a) More
b) Less
c) Double
d) None of the mentioned
Answer: a
Explanation: In orthogonal signalling with symbols having more number of bits need more power but requirement per bit is reduced.
18. For FSK signalling, WT is equal to
a) 0
b) 1
c) 0.737
d) Infinity
Answer: b
Explanation: For FSK signalling the detection bandwidth is typically equal to symbol rate 1/T that is WT is nearly equal to 1.
19. Energy per symbol Es is given as
a) Es=Eb(log2M)
b) Es=Eb/(log2M)
c) Es=2Eb(log2M)
d) Es=Eb/2(log2M)
Answer: a
Explanation: In M-ary PSK signalling, the energy per symbol is given as Es=Eb(log2M).
20. The relation between the probability of bit error and probability of symbol error in M-ary orthogonal signalling is
a) M/M-1
b) 2M/M-1
c) (M/2)/M-1
d) M/M+1
Answer: c
Explanation: The relationship between the probability of bit error and probability of symbol error is (M/2)/M-1 in M-ary orthogonal signalling.
21. As limit of k increases, the ratio of PB/PE becomes
a) 1:2
b) 2:1
c) 1:3
d) 3:1
Answer: a
Explanation: As the limit of k increases, the ratio of PB/PE becomes 1:2.
21. In M-ary FSK, as M increases error
a) Increases
b) Decreases
c) Does not get effected
d) Cannot be determined
Answer: b
Explanation: In M-ary FSK as M increases error decreases.
22. In M-ary FSK as M tends to infinity, probability of error tends to
a) Infinity
b) Unity
c) Zero
d) None of the mentioned
Answer: c
Explanation: In M-ary FSK as M tends to infinity, probability of error becomes zero.
23. For non coherent reception of PSK _____ is used.
a) Differential encoding
b) Decoding
c) Differential encoding & Decoding
d) None of the mentioned
Answer: c
Explanation: For non coherent reception of PSK, differential encoding is used at the transmitter and decoding is used at the receiver.
24. Which modulation technique have the same bit and symbol error probability?
a) BPSK
b) DPSK
c) OOK
d) All of the mentioned
Answer: d
Explanation: BPSK, DPSK, OOK and non coherent FSK have same bit and symbol error probability.
25. An amplifier uses ______ to take input signal.
a) DC power
b) AC power
c) DC & AC power
d) None of the mentioned
Answer: a
Explanation: An amplifier uses DC power to take an input signal and increase its amplitude at the output.
26. Which has 50% maximum power efficiency?
a) Class A
b) Class B
c) Class AB
d) None of the mentioned
Answer: a
Explanation: Class A amplifiers have 50% maximum power efficiency.
27. Which generates high distortion?
a) Class A
b) Class B
c) Class C
d) Class AB
Answer: c
Explanation: Class C amplifiers generate high distortion and it is closer to switch than an amplifier.
28. Class B linear amplifiers have maximum power efficiency of
a) 50%
b) 75%
c) 78.5%
d) None of the mentioned
Answer: c
Explanation: Class B linear amplifiers have maximum power efficiency of 78.5%.
29. Which has the maximum power efficiency?
a) Class A
b) Class B
c) Class C
d) Class AB
Answer: c
Explanation: Class C has the maximum power efficiency when compared to the other linear amplifiers.
30. Free space in idealization which consists
a) Transmitter
b) Receiver
c) Transmitter & Receiver
d) None of the mentioned
Answer: c
Explanation: Free space is an idealization that consists of only transmitter and receiver.
31. Average energy per bit is given by
a) average energy symbol/log2 M
b) average energy symbol * log2 M
c) log2 M/ Average energy symbol
d) none of the mentioned
Answer: a
Explanation: Average energy per bit is given by average energy symbol divided by log2 M.
32. Which FSK has no phase discontinuity?
a) Continuous FSK
b) Discrete FSK
c) Uniform FSK
d) None of the mentioned
Answer: a
Explanation: Continuous frequency shift keying has no phase discontinuity between symbols.
33. FSK reception is
a) Phase Coherent
b) Phase non coherent
c) Phase Coherent & non coherent
d) None of the mentioned
Answer: c
Explanation: Reception of FSK can be either phase coherent or phase non coherent.
34. FSK reception uses
a) Correlation receiver
b) PLL
c) Correlation receiver & PLL
d) None of the mentioned
Answer: c
Explanation: Frequency shift keying uses correlation receiver and phase locked loop.
35. In non coherent reception _____ is measured.
a) Phase
b) Energy
c) Power
d) None of the mentioned
Answer: b
Explanation: In non coherent reception of FSK, energy in each frequency is measured.
36. Every frequency has ____ orthogonal functions.
a) One
b) Two
c) Four
d) Six
Answer: b
Explanation: Every frequency has two orthogonal functions – sine and cosine.
37. If we correlate the received signal with any one of the two orthogonal function, the obtained inner product will be
a) In phase
b) Quadrature
c) Zero
d) Cannot be determined
Answer: c
Explanation: If we correlate the received signal with only one of the orthogonal function for example sine, the inner product obtained will be zero.
38. If we correlate the received signal with both orthogonal function the inner product will be
a) In phase
b) Quadrature
c) In phase and quadrature
d) Unity
Answer: c
Explanation: If we correlate the received signal with both the orthogonal function, the two inner products obtained will be in phase and quadrature.
39. Simulation is used to determine
a) Bit error rate
b) Symbol error rate
c) Bit error
d) Symbol error
Answer: a
Explanation: A simulation of digital communication system is used to estimate bit error rate.
40. Matched filter is a _____ technique.
a) Modulation
b) Demodulation
c) Modulation & Demodulation
d) None of the mentioned
Answer: b
Explanation: Matched filter is a demodulation technique with LTI.
41. Which is called as on-off keying?
a) Amplitude shift keying
b) Uni-polar PAM
c) Amplitude shift keying & Uni-polar PAM
d) None of the mentioned
Answer: c
Explanation: Amplitude shift keying and uni-polar PAM both schemes are called as on off keying.
42. QAM uses ______ as the dimensions.
a) In phase
b) Quadrature
c) In phase & Quadrature
d) None of the mentioned
Answer: c
Explanation: QAM uses in phase and quadrature which is cosine and sine respectively as the dimensions.
43. Which has same probability of error?
a) BPSK and QPSK
b) BPSK and ASK
c) BPSK and PAM
d) BPSK and QAM
Answer: c
Explanation: BPSK is similar to bipolar PAM and both have same probability of error.
44. Which system uses QAM?
a) Digital microwave relay
b) Dial up modem
c) Digital microwave relay & Dial up modem
d) None of the mentioned
Answer: c
Explanation: Digital microwave relay, dial up modem and etc uses QAM modulation technique.
45.In On- Off keying, the carrier signal is transmitted with signal value 1 and '0' indicates a) No carrier b) Half the carrier amplitude c) Amplitude of modulating signal d) None of the above ANSWER: a) No carrier 45.ASK modulated signal has the bandwidth a) Same as the bandwidth of baseband signal b) Half the bandwidth of baseband signal c) Double the bandwidth of baseband signal d) None of the above ANSWER: a) Same as the bandwidth of baseband signal46.Coherent detection of binary ASK signal requires a) Phase synchronization b) Timing synchronization c) Amplitude synchronization d) Both a) and b) ANSWER: d) Both a) and b) 47.The probability of error of DPSK is ______________ than that of BPSK. a) Higher b) Lower c) Same d) Not predictable ANSWER: a) Higher 48.In Binary Phase Shift Keying system, the binary symbols 1 and 0 are represented by carrier with phase shift of a) Π/2 b) Π c) 2Π d) 0 ANSWER: Π
49.BPSK system modulates at the rate of a) 1 bit/ symbol b) 2 bit/ symbol c) 4 bit/ symbol d) None of the above ANSWER: a) 1 bit/ symbol
1. The method in which the tail of one pulse smears into adjacent symbol interval is called as
a) Intersymbol interference
b) Interbit interference
c) Interchannel interference
d) None of the mentioned
Answer: a
Explanation: Due to the effect of system filtering the received pulse can overlap on one and another. The tail of one pulse smears into the adjacent symbol interval thereby interfering the detection process. This process is called as intersymbol interference.
2. If each pulse of the sequence to be detected is in _____ shape, the pulse can be detected without ISI.
a) Sine
b) Cosine
c) Sinc
d) None of the mentioned
Answer: c
Explanation: The sinc shaped pulse is the ideal nyquist pulse. If each pulse in the sequence to be detected is in sinc shape the pulses can be detected without ISI.
3. What is symbol rate packing?
a) Maximum possible symbol transmission rate
b) Maximum possible symbol receiving rate
c) Maximum bandwidth
d) Maximum ISI value allowed
Answer: a
Explanation: A system with bandwidth Rs/2 can support a maximum transmission rate of Rs without ISI. Thus for ideal Nyquist filtering the maximum possible symbol transmission rate is called as symbol rate packing and it is equal to 2 symbols/s/Hz.
4. A nyquist pulse is the one which can be represented by _____ shaped pulse multiplied by another time function.
a) Sine
b) Cosine
c) Sinc
d) None of the mentioned
Answer: c
Explanation: A nyquist filter is one whose frequency transfer function can be represented by a rectangular function convolved with any real even symmetric frequency function and a nyquist pulse is one whose shape can be represented by sinc function multiplied by another time function.
5. Examples of nyquist filters are
a) Root raised cosine filter
b) Raised cosine filter
c) Root raised & Raised cosine filter
d) None of the mentioned
Answer: c
Explanation: The most popular among the class of nyquist filters are raised cosine and root raised cosine filter.
6. The minimum nyquist bandwidth for the rectangular spectrum in raised cosine filter is
a) 2T
b) 1/2T
c) T2
d) 2/T
Answer: b
Explanation: For raised cosine spectrum the minimum nyquist bandwidth is equal to 1/2T.
7. Roll off factor is the fraction of
a) Excess bandwidth and absolute bandwidth
b) Excess bandwidth and minimum nyquist bandwidth
c) Absolute bandwidth and minimum nyquist bandwidth
d) None of the mentioned
Answer: b
Explanation: The roll off factor is defined by a fraction of excess bandwidth and the minimum nyquist bandwith. It ranges from 0 to 1.
8. Which value of r (roll off factor) is considered as Nyquist minimum bandwidth case?
a) 0
b) 1
c) Infinity
d) None of the mentioned
Answer: a
Explanation: For the roll off factor of 0 an ideal rectangular nyquist pulse is obtained. This is called as nyquist minimum bandwidth case.
9. A pulse shaping filter should satisfy two requirements. They are
a) Should be realizable
b) Should have proper roll off factor
c) Should be realizable & have proper roll off factor
d) None of the mentioned
Answer: c
Explanation: A pulse shaping filter should provide the desired roll off and should be realizable, that is the impulse response needs to be truncated to a finite length.
10. Examples of double side band signals are
a) ASK
b) PSK
c) ASK & PSK
d) None of the mentioned
Answer: c
Explanation: ASK and PSK needs twice the transmission bandwidth of equivalent baseband signals. Thus these are called as double side band signals.
11. Channel’s phase response must be a linear function of
a) Time
b) Frequency
c) Time & Frequency
d) None of the mentioned
Answer: b
Explanation: To achieve ideal transmission characteristics, the signal’s bandwidth must be constant and the channel’s phase response must be a linear function of frequency.
12. Amplitude distortion occurs when
a) Impulse response is not constant
b) Impulse response is constant
c) Frequency transfer function is constant
d) Frequency transfer function is not constant
Answer: d
Explanation: When modulus of channel’s transfer function is not constant within W then amplitude distortion occurs.
13. Phase distortion occurs when
a) Phase response is function of frequency
b) Phase response is not a function of frequency
c) All of the mentioned
d) None of the mentioned
Answer: b
Explanation: When channels phase response is not a linear function of frequency within W then phase distortion occurs.
14. Equalization process includes
a) Maximum likelihood sequence estimation
b) Equalization with filters
c) Maximum likelihood sequence estimation & Equalization with filters
d) None of the mentioned
Answer: c
Explanation: Equalization process can be divided into two major categories called as maximum likelihood sequence estimator and equalizer with a filter.
15. The maximum likelihood sequence estimator adjusts _______ according to _____ environment.
a) Receiver, transmitter
b) Transmitter, receiver
c) Receiver, receiver
d) None of the mentioned
Answer: a
Explanation: In maximum likelihood sequence estimator it measures the impulse response value and adjusts the receiver environment according to that of the transmitter.
16. The filters used with the equalizer is of ______ types.
a) Feed forward
b) Feed backward
c) Feed forward and feedback
d) None of the mentioned
Answer: c
Explanation: The filters used with equalizers can be linear devices that contain only feed forward elements or non linear devices with both feed forward and feed back elements.
17. Transversal equalizers are ________ and decision feedback equalizers are ______
a) Feed forward, feed back
b) Feed back, feed forward
c) Feed forward, feed forward
d) Feedback, feedback
Answer: a
Explanation: Linear devices with only feed forward elements are called as transversal equalizers and non linear devices with both feed forward and feed back elements are called as decision feedback equalizers.
18. Symbol spaced has ____ sample per symbol and fractionally spaced has ___ samples per symbol.
a) One, many
b) Many, one
c) One, one
d) Many, many
Answer: a
Explanation: Predetection samples are provided only on symbol boundaries. A condition in which only one sample per symbol are provided is called as symbol spaced and the condition in which multiple samples are provided per symbol is called as fractionally spaced.
19. The _______ of the opening of eye pattern indicates the time over which the sampling for detection might be performed.
a) Length
b) Width
c) X-axis value
d) Y-axis value
Answer: b
Explanation: An eye pattern is a display that results from measuring a system’s response to baseband signals in a prescribed way. The width of the opening gives the time over which the sampling for detection might be performed.
20. Range of time difference of the zero crossing gives the value of
a) Width
b) Distortion
c) Timing jitter
d) Noise margin
Answer: c
Explanation: The time difference of the zero crossing in the eye pattern gives the value of timing jitter.
21.As the eye opens, ISI _______
a. Increases
b. Decreases
c. Remains the same
d. None of the mentioned
Answer: Option 2- Decreases
22.The _______ of the opening of eye pattern indicates the time over which the sampling for detection
might be performed.
a. Length
b. Width
c. X-axis value
d. Y-axis value
Answer: Option 2 – Width
23. A nyquist pulse is the one which can be represented by _____ shaped pulse multiplied by another time
function.
a. Sine
b. Cosine
c. Sinc
d. None of the mentioned
Answer: Option 3 – Sinc
24. Which value of r (roll off factor) is considered as Nyquist minimum bandwidth case?
a. 0
b. 1
c. Infinity
d. None of the mentioned
Answer: Option 1 – 0
25.Examples of nyquist filters are
a. Root raised cosine filter
b. Raised cosine filter
c. Root raised & Raised cosine filter
d. None of the mentioned
Answer: Option 3 – Root raised & Raised cosine filter
1. ____________ limits receiver sensitivity.
a) Noise
b) Depletion layer
c) Avalanche
d) Current
Answer: a
Explanation: Receiver noise affects receiver sensitivity. It can dictate the overall system design. The noise can be temperature, environmental factor or due to components.
2. A ____________ performs the linear conversion of the received optical signal into an electric current.
a) Receiver
b) Converter
c) Detector
d) Reflector
Answer: c
Explanation: An optical signal is always fed to a detector. A detector is an optoelectronic converter which linearly converts the received optical signal into an electric current.
3. __________ are provided to reduce distortion and to provide a suitable signal shape for the filter.
a) Detector
b) Equalizer
c) Filters
d) Amplifier
Answer: b
Explanation: Optical detectors are linear devices. They do not introduce distortion themselves but other components may exhibit nonlinear behaviour. To compensate for distortion, an equalizer is provided in the receiver circuit.
4. A _________ maximizes the received signal-to-noise ratio in the receiver circuitry.
a) Filter
b) Equalizer
c) Detector
d) Reflector
Answer: a
Explanation: A filter reduces the noise bandwidth as well as inbounds noise levels. A filter maximizes the received signal-to-noise ratio while preserving the essential features of the signal. It also reduces ISI.
5. ________ can be operated in three connections.
a) Reflectors
b) Diodes
c) LED’s
d) FET’s
Answer: d
Explanation: FET’s or bipolar transistors are operated in three useful connections. These are the common emitter, the common base or gate, and the emitter or source follower.
6. How many structures of pre-amplifiers exist?
a) Two
b) Three
c) Four
d) One
Answer: b
Explanation: The basic structures of pre-amplifiers are observed in three forms. These are low-impedance, high-impedance and trans-impedance front end preamplifier structures.
7. What is the main factor contributing to the choice of the operational amplifier?
a) Gain
b) Impedance
c) Conductance
d) Gain-Bandwidth product
Answer: d
Explanation: A TTL interface stage is always used with the operational amplifier. A device that requires higher accuracy often tends to depend on gain-bandwidth product.
The choice of amplifier for receiver accuracy is dependant on gain-bandwidth product.
8. The multiplication factor for the APD varies with the device temperature.
a) True
b) False
Answer: a
Explanation: Optimum multiplication factor is required for smooth voltage variance. The multiplication factor for APD varies with the device temperature thus making provision of fine control for bias voltage.
9. How many categories of dynamic gain equalizers are available?
a) One
b) Two
c) Three
d) Four
Answer: b
Explanation: Dynamic gain equalizers are categorized into two types. These are single-channel and multichannel equalizers, thus providing operation using single or multiple wavelengths.
10. How many simultaneous channels can be provided in a band DGE(Dynamic gain equalizer)?
a) Six
b) Two
c) Eight
d) Ten
Answer: c
Explanation: Generally, eight channels are provided simultaneously in a band DGE. These are for the attenuation purpose of channels along with gain equalization.
11. Matched filter may be optimally used only for
a) Gaussian noise
b) Transit time noise
c) Flicker
d) All of the above
ANSWER: a) Gaussian noise
12. Characteristics of Matched filter are
a) Matched filter is used to maximize Signal to noise ratio even for non Gaussian noise
b) It gives the output as signal energy in the absence of noise
c) They are used for signal detection
d) All of the above
ANSWER: d) All of the above
13. Matched filters may be used
a) To estimate the frequency of the received signal
b) In parameter estimation problems
c) To estimate the distance of the object
d) All of the above
ANSWER: d) All of the above
Prepare For Your Placements: https://lastmomenttuitions.com/courses/placement-preparation/
![]()
/ Youtube Channel: https://www.youtube.com/channel/UCGFNZxMqKLsqWERX_N2f08Q
Follow For Latest Updates, Study Tips & More Content!
Not a member yet? Register now
Are you a member? Login now